Let's try to analyze what Identity and Access Management (Idm/Idam/IAM) is all about, why would organization care for it and the benefits it offers.
What is Identity and Access Management-
Identity and Access Management deals with managing the identity and access of an entity. The entity could be individual user or an application which interacts with a system/organization.The following figure shows the main components of the Identity and Access Management Framework.
With the evolution of web 2.0 and cloud identity management the situation doesn't get any better, the number of logins and passwords that employees must use on a daily basis has escalated and is a growing source of frustration and lost productivity. Worst of all, there’s the temptation to use the same password for all applications or to write down SaaS passwords on a sticky note, creating security risks that most organizations are trying to avoid.
In addition to the core services the app provides it also has to manage additional functions related to user management and access management.
Simplified Solution with Identity and Access Management system in place
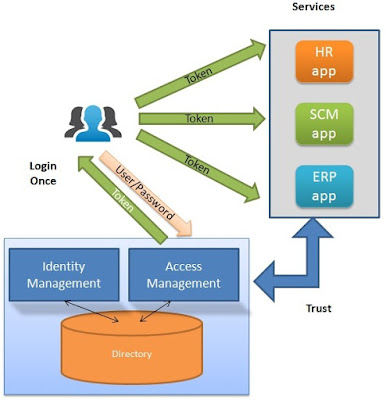
How Identity and Access Management systems works
What is Identity and Access Management-
Identity and Access Management deals with managing the identity and access of an entity. The entity could be individual user or an application which interacts with a system/organization.The following figure shows the main components of the Identity and Access Management Framework.
There are several technologies and security standards which are used to implement Idm like - SSO, SAML, WS-Federation, JWT, STS, OAuth, OpenID, Directory services, WS-Trust, WS-Security just to list a few. Instead of going into details of each of them let's understand the basic concepts which forms the basis of Identity and access management
- Authentication - who you are
- Authorization/Access control - what you are authorized to do
- Single Sign on - login once
- Role Based identity - users can be grouped together based on role e.g admin, HR roles
- directory - users repository
- Provisioning - The process of creating identities, defining their access privileges and adding them to an ID repository/directory.
- de-provisioning - The process of removing an identity from an ID repository and terminating access privileges.
- identity life cycle - managing user identity flow - Provisioning (when users joins the system), maintaining access (as they interact with system) and de-provisiong (once they leaves the system)
- Federated Identity - sharing identity across systems and enterprise boundaries.
Need for Identity and Access Management
Before going into details of how identity management systems works let's analyze the need for it. Here is a very simple example.
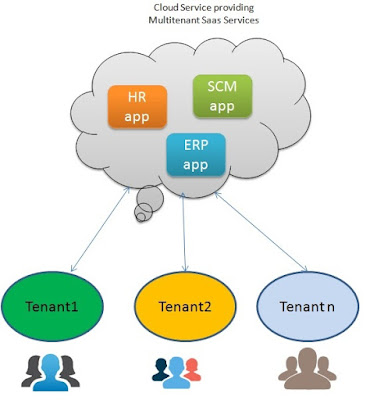
The following picture shows services offered by an enterprise/organization e.g HR apps, Supply chain management apps and ERP apps. These apps are accessed by users/partners/contractors. When a user wish to access an app she authenticates using her credentials (username/password), the app than validates the credentials and allow/disallow access to the app and its resources. Also the apps are accessible to specific users who belongs to that role. Human Resources guys should access HR apps Sales guys should be allowed to access Sales App and so on. If a user have access to different app she need to create login with each app, have to remember password for each of them. This gets too complicated when the number of users and apps/services increases.
The following picture shows services offered by an enterprise/organization e.g HR apps, Supply chain management apps and ERP apps. These apps are accessed by users/partners/contractors. When a user wish to access an app she authenticates using her credentials (username/password), the app than validates the credentials and allow/disallow access to the app and its resources. Also the apps are accessible to specific users who belongs to that role. Human Resources guys should access HR apps Sales guys should be allowed to access Sales App and so on. If a user have access to different app she need to create login with each app, have to remember password for each of them. This gets too complicated when the number of users and apps/services increases.

With the evolution of web 2.0 and cloud identity management the situation doesn't get any better, the number of logins and passwords that employees must use on a daily basis has escalated and is a growing source of frustration and lost productivity. Worst of all, there’s the temptation to use the same password for all applications or to write down SaaS passwords on a sticky note, creating security risks that most organizations are trying to avoid.
In addition to the core services the app provides it also has to manage additional functions related to user management and access management.
Simplified Solution with Identity and Access Management system in place

- Identity and Access Management pushed to IDAM system
- Login Once - smoother login experience, no need to remember multiple passwords,
- Token based access - applications don't have to manage user authentication but rely on security tokens offered by Access management component to check user authn and authz
- Identity life cycle management - deals with managing user identity flow - Provisioning (when users joins the system), maintaining access (as they interact with system) and de-provisiong (once they leaves the system)
How Identity and Access Management systems works
A typical ID management system today comprises four basic elements: a directory of the personal data the system uses to define individual users (think of it as an ID repository); a set of tools for adding, modifying and deleting that data (the access life cycle management stuff); a system that regulates user access (enforcement of security policies and access privileges); and an auditing and reporting system (so you'll have a way to verify what's actually been happening on your system).
Identity Life cycle
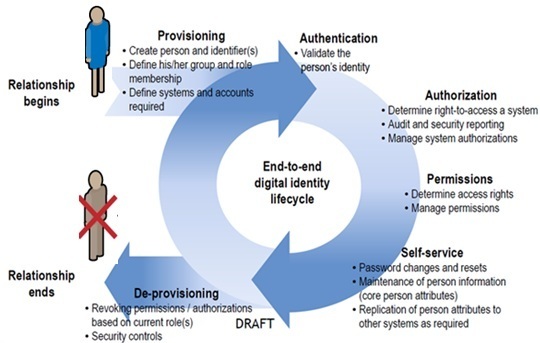
Identity Life cycle



This comment has been removed by the author.
ReplyDeleteUseful Information,Thanks for sharing!!!
ReplyDeleteAccess Control Solution
Biometric Attendance Solution
Canteen Management Solution
Contract Management Solution
Visitor Management System
Get a reliable solution for IT transformation automation. We are a Silicon Valley-based startup Software Company located in the San Francisco Bay Area in California.
ReplyDelete