In my previous blog i explained about OAuth2 protocol. In this blog i will explain how you can use Oracle OAuth2 support (provided in 11gPS6 patch set and PS7 release) to secure your applications that are deployed on-premise or cloud.
I will be explaining 2- legged OAuth2 flow using client credentials grant
Use case
The above picture presents a high level overview of a SaaS app calling REST service. The SaaS app could be any Multi tenant cloud enabled app e.g. CRM/ ERP available over cloud. The SaaS app internally may be using BPEL process. In this example the SaaS app is deployed as a Oracle SOA composite app
The client and Service app are secured with OWSM Agent OAuth2 security policies.
1) OWSM Client Agent sends request for OAuth2 AT (JWT) by sending authorization grant using standard OAuth2 flows. The authorization request is signed using OWSM client’s Private Key.
2) OAuth2 Service verifies OWSM Client request and responds with a signed Access Token (JWT).
3) OWSM client propagates this AT to Service secured with OWSM Service Agent.
4) OWSM Service agent verifies the AT and responds with a valid response or errors out in case AT does not verify.
1) Enabling OAM OAuth2 Service
2) Configuring OAuth2 Service
3) Registering your app with OAM OAuth2 service
4) Requesting token using client credentials grant - Basic Auth
5) Securing Service App (RESTful Service) with OWSM OAuth2 Security policies
6) Securing Client app (SOA) with OWSM OAuth2 Security policies
7) Establishing trust
8) Deploying and Test your apps.
This assumes that you have already installed and configured Oracle Access Manager server, For details on installing and configuring Oracle IDM product suite you can refer to this blog post
1.2) Oracle Access Management 11.1.2.3 introduces a redesigned Oracle Access Management Console. This new Console displays a Launch Pad and subsequent pages based on the Administration Role to which a user is assigned a successful login.
1.3) Click on Mobile Security - > Mobile OAuth Services
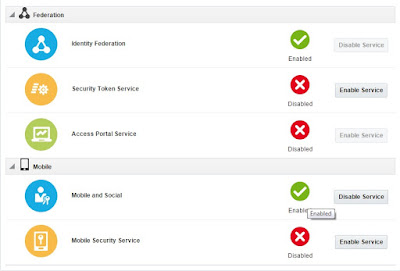
1.4) The console will show the list of Services , Enable - Mobile and Social. This should OAuth2 service. A green check mark in the Status field beside the service name indicates the service is enabled. A red circle with a cross through it indicates that the corresponding service is disabled.
2.2) You can either create a new Identity domain or use the out of box Default domain.
2.3) Default domain -> Service Profiles -> OAuthServiceProfile
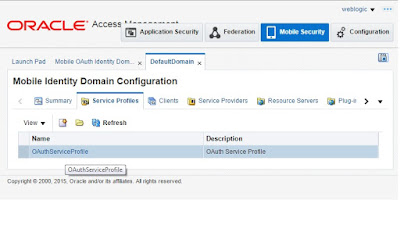
2.4) This shows the default token settings which you can configure e.g.token expiry for various authz grants.
2.5) You can also configure the trusted issuers. Please check the URL of OAuth2 service Endpoint which client will use for sending Access Token request.
3.2) Register you client. Provide name and description. OAM OAuth server generates a random unique client id and client secret for the client. Once can choose to provide user defined value.
For e.g.
Client ID - mycustomId
Client Secret - v1rCJvxbtMKeaiDduk
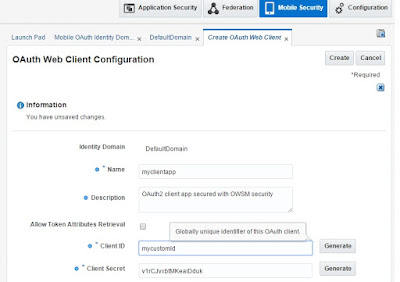
3.3) Ensure the required Grant types are selected. You can also configure Scope. Using allow access to all scope option for this use case.
This should
Here client ID and Client Secret are passed in base64 encoded format as part of Authorization header.
OAuth2 Server token endpoint - >
http://slc06uwa.us.oracle.com:14100/ms_oauth/oauth2/endpoints/oauthservice/tokens
You can use any tool to encode client credentials registered with OAuth2 server in step 3.2 in following format - ClientId:ClientSecret.
The OAuth2 server should respond with an Access Token which is a JWT e.g. -
You can also use GPA feature (beyond the scope of this blog) to secure your REST services.
4.2) Select OWSM OAuth2 client policies
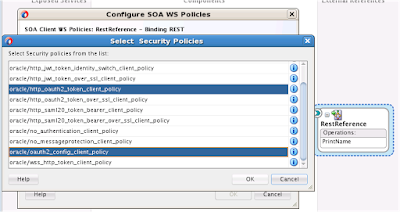
4.3) Click on Edit config override property for oauth2_config_client_policy
4.4) Override token.uri to OAuth2 server endpoint
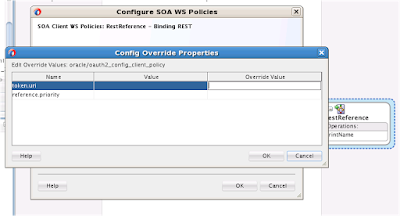
Here token.uri must point to the OAuth2 server endpoint URL. In this example endpoint URL is http://slc06uwa.us.oracle.com:14100/ms_oauth/oauth2/endpoints/oauthservice/tokens
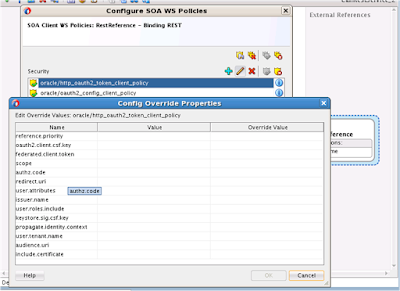
4.5)Edit config override for http_oauth2_token_client_policy if you wish to override default configuration.I will use the default.
I will be explaining 2- legged OAuth2 flow using client credentials grant
Use case
The above picture presents a high level overview of a SaaS app calling REST service. The SaaS app could be any Multi tenant cloud enabled app e.g. CRM/ ERP available over cloud. The SaaS app internally may be using BPEL process. In this example the SaaS app is deployed as a Oracle SOA composite app
In order to leverage OWSM OAuth2 security feature you need to have Oracle Access Manager (OAM) installed in your env which provides OAuth2 services.
Token flow
The following picture shows the token flow b/w OAuth2 sever client app and service.The client and Service app are secured with OWSM Agent OAuth2 security policies.
1) OWSM Client Agent sends request for OAuth2 AT (JWT) by sending authorization grant using standard OAuth2 flows. The authorization request is signed using OWSM client’s Private Key.
2) OAuth2 Service verifies OWSM Client request and responds with a signed Access Token (JWT).
3) OWSM client propagates this AT to Service secured with OWSM Service Agent.
4) OWSM Service agent verifies the AT and responds with a valid response or errors out in case AT does not verify.
1) Enabling OAM OAuth2 Service
2) Configuring OAuth2 Service
3) Registering your app with OAM OAuth2 service
4) Requesting token using client credentials grant - Basic Auth
5) Securing Service App (RESTful Service) with OWSM OAuth2 Security policies
6) Securing Client app (SOA) with OWSM OAuth2 Security policies
7) Establishing trust
8) Deploying and Test your apps.
1) Enable OAM OAuth2 Service
1.1) Login to OAM console.This assumes that you have already installed and configured Oracle Access Manager server, For details on installing and configuring Oracle IDM product suite you can refer to this blog post

1.2) Oracle Access Management 11.1.2.3 introduces a redesigned Oracle Access Management Console. This new Console displays a Launch Pad and subsequent pages based on the Administration Role to which a user is assigned a successful login.

1.3) Click on Mobile Security - > Mobile OAuth Services

1.4) The console will show the list of Services , Enable - Mobile and Social. This should OAuth2 service. A green check mark in the Status field beside the service name indicates the service is enabled. A red circle with a cross through it indicates that the corresponding service is disabled.

2) Configure OAM OAuth2 Service
2.1) Under OAM Console -> Mobile Security - > Mobile OAuth Services
2.2) You can either create a new Identity domain or use the out of box Default domain.

2.3) Default domain -> Service Profiles -> OAuthServiceProfile

2.4) This shows the default token settings which you can configure e.g.token expiry for various authz grants.
2.5) You can also configure the trusted issuers. Please check the URL of OAuth2 service Endpoint which client will use for sending Access Token request.

3) Register your application
3.1) Default domain-> Clients - > OAuth Web client - > CreateFor e.g.
Client ID - mycustomId
Client Secret - v1rCJvxbtMKeaiDduk

3.3) Ensure the required Grant types are selected. You can also configure Scope. Using allow access to all scope option for this use case.
4) Requesting token using client credentials grant - Basic Auth
You can use the following curl command to get AT from OAuth2 server -
curl -i -H 'Authorization: Basic
bXljdXN0b21JZDp2MXJDSnZ4YnRNS2VhaURkdWs=' -H 'ContentType:
x-www-form-urlencoded' --request POST
'http://slc06uwa.us.oracle.com:14100/ms_oauth/oauth2/endpoints/oauthservice/tokens'
-d 'grant_type=client_credentials'
|
This should
Here client ID and Client Secret are passed in base64 encoded format as part of Authorization header.
OAuth2 Server token endpoint - >
http://slc06uwa.us.oracle.com:14100/ms_oauth/oauth2/endpoints/oauthservice/tokens
You can use any tool to encode client credentials registered with OAuth2 server in step 3.2 in following format - ClientId:ClientSecret.
The OAuth2 server should respond with an Access Token which is a JWT e.g. -
HTTP/1.1 200 OK
Date: Wed, 05 Aug 2015 16:04:52 GMT
Content-Type: application/json
{"oracle_client_assertion_type":"urn:ietf:params:oauth:client-assertion-type:jwt-bearer","expires_in":604800,"token_type":"Bearer","oracle_tk_context":
"client_assertion","access_token":"eyJhbGcidHp[…..]zzi4BCjHY"}
|
Now let's see how to use OWSM Oauth2 securit policies with your client and service apps,
5) Secure REST Service using OWSM OAuth2 security policy.
Policy
|
Description
|
oracle/
multi_token_rest_service_policy
|
This policy verifies the Access Token sent from client app.
|
Attach oracle/multi_token_rest_service_policy by updating web.xml file of REST application
The following provides an example of how to update the web.xml file.
<?xml version = '1.0'
encoding = 'windows-1252'?>
<web-app
xmlns="http://java.sun.com/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://java.sun.com/xml/ns/javaee
http://java.sun.com/xml/ns/javaee/web-app_2_5.xsd"
version="2.5">
<servlet>
<servlet-name>helloworld</servlet-name>
<servlet-class>com.sun.jersey.spi.container.servlet.ServletContainer</servlet-class>
<load-on-startup>1</load-on-startup>
</servlet>
<servlet-mapping>
<servlet-name>helloworld</servlet-name>
<url-pattern>/restservice/*</url-pattern>
</servlet-mapping>
<!--OWSM Security Filter entry-->
<filter-mapping>
<filter-name>OWSMSecurityFilter</filter-name>
<servlet-name>helloworld</servlet-name>
</filter-mapping>
<filter>
<filter-name>OWSMSecurityFilter</filter-name>
<filter-class>oracle.wsm.agent.handler.servlet.SecurityFilter</filter-class>
<init-param>
<param-name>servlet-name</param-name>
<param-value>helloworld</param-value>
</init-param>
<init-param>
<param-name>oracle.wsm.metadata.policySet</param-name>
<param-value><![CDATA[<sca11:policySet name="policySet"
appliesTo="REST-Resource()" attachTo="Service('*')"
xmlns:sca11="http://docs.oasis-open.org/ns/opencsa/sca/200903"
xmlns:orawsp="http://schemas.oracle.com/ws/2006/01/policy"
xmlns:wsp15="http://www.w3.org/ns/ws-policy">
<wsp15:PolicyReference
URI="oracle/multi_token_rest_service_policy"
orawsp:category="security" orawsp:status="enabled">
</wsp15:PolicyReference>
</sca11:policySet>]]>
</param-value>
</init-param>
</filter>
</web-app>
|
||
You can also use GPA feature (beyond the scope of this blog) to secure your REST services.
6) Secure Client (SOA app) using OWSM OAuth2 Security
You can secure your SOA app at design time using J developer.
4.1) Secure SOA Reference WS Binding (client) - Right click - > Configure SOA WS Policies
4.2) Select OWSM OAuth2 client policies

4.3) Click on Edit config override property for oauth2_config_client_policy
4.4) Override token.uri to OAuth2 server endpoint

Here token.uri must point to the OAuth2 server endpoint URL. In this example endpoint URL is http://slc06uwa.us.oracle.com:14100/ms_oauth/oauth2/endpoints/oauthservice/tokens
4.5)Edit config override for http_oauth2_token_client_policy if you wish to override default configuration.I will use the default.

5) Establish Trust
In above flow there are 3 main components involved.
1) OAM OAuth2 server
2) SaaS app
3) REST sevice
5.1) Trust between OAuth2 server and client
In order to verify the OWSM client (signed) request for
Access Token OAuth2 service should have the public key certificate
corresponding to the private key used to sign the request in its keystore.
OAuth2 server responds with a signed access token
5.2) Trust between OAuth2 server and Service
The service must also trust the Access Token (signed) sent from OAuth2 server.To set up trust between OAuth2 server and service import
the OAuth2 server signing certificate into resource server keystore.
6) Deploy and Test your apps.
That's it you can now deploy and Test your apps.
I have tried to touch upon the high level steps and configuration you require to use OAuth2 security. There are a number of fine level security configuration which you can configure like setting trusted issuers, setting scope, switching identity, setting up SSL etc just to name a few.
I have tried to touch upon the high level steps and configuration you require to use OAuth2 security. There are a number of fine level security configuration which you can configure like setting trusted issuers, setting scope, switching identity, setting up SSL etc just to name a few.










I am getting below error while executing curl command.
ReplyDeleteHTTP/1.1 500 Internal Server Error
Cache-Control: no-cache, no-store, must-revalidate
Date: Tue, 30 Aug 2016 10:31:01 GMT
Pragma: no-cache
Transfer-Encoding: chunked
Content-Type: application/json
X-ORACLE-DMS-ECID: 4897a9aa57db388b:-545a547d:156d5cacaed:-8000-0000000000001ed6
X-Powered-By: Servlet/2.5 JSP/2.1
{"error":"server_error", "error_description":"Server unable to handle the request due to erroneous input or server side issue"}
Can you explain in more details how to set up the following tasks?
ReplyDelete5.1) Trust between OAuth2 server and client
In order to verify the OWSM client (signed) request for Access Token OAuth2 service should have the public key certificate corresponding to the private key used to sign the request in its keystore.
OAuth2 server responds with a signed access token
5.2) Trust between OAuth2 server and Service
The service must also trust the Access Token (signed) sent from OAuth2 server.To set up trust between OAuth2 server and service import the OAuth2 server signing certificate into resource server keystore.
hi Danny,
DeleteWere you able to figure out how to Trust between OAuth2 server and Service.
I am also facing the same problem and any help is much appreciated.
Hi Gaurav,
ReplyDeleteCould you please help us - what is the configuration required in OWSM to secure Proxy Services (REST services) using OAuth2 of OAM.
How does the token validation takes place.
smm panel
ReplyDeleteSmm panel
iş ilanları
instagram takipçi satın al
https://www.hirdavatciburada.com/
beyazesyateknikservisi.com.tr
SERVİS
Tiktok jeton hile