In this blog i will explain how you can expose your existing SOAP services as REST services using Oracle Service Bus 12c.
Business challenge
Company X provides SOAP based business services which are consumed by existing consumers. The business service is exposed using oracle service bus. With the focus on mobile clients it becomes important to expose these services as REST APIs to support new consumers at the same time ensuring that existing customers (SOAP clients) are not impacted.
As a service producer you want to ensure that your existing service can be consumed by new consumers without making any changes to the business backend service.

Solution
Oracle Service Bus addresses these challenges with minimum effort. To show this let's take a simple example. In this example we use a Credit Card validation service as the business back end service which is virtualized using Oracle Service Bus.
Clients do not call the service directly but via proxy services defined within OSB which routes the request to backend service via business service. Since we are using Oracle Service Bus we can simply add a new REST based proxy service to support our use case. Let's see how.
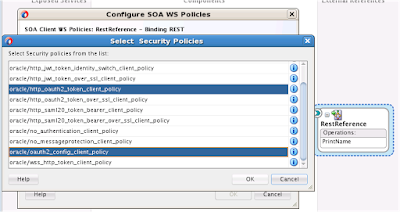
To expose your back-end service as REST serve all you need to do is right click on OSB pipeline and select "Expose as REST" option.
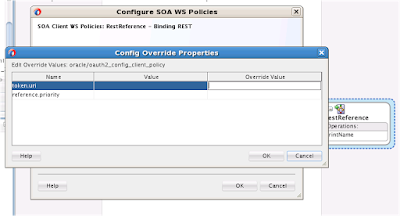
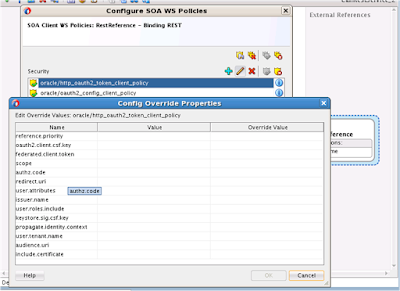
This should open a dialog box where you can specify REST binding properties like name, arguments, HTTP method type etc.
This should generate the corresponding proxy service for REST
Now as you can see the Oracle service bus exposed 2 proxy services to which service consumers can connect to, one REST proxy and other the existing SOAP proxy service.
You can test your REST proxy by doing a right click and select run.
Once you click on execute you you can see the response with status as Authorized. Thats all, you have successful ly exposed your backend service as REST service using few clicks only.
Business challenge
Company X provides SOAP based business services which are consumed by existing consumers. The business service is exposed using oracle service bus. With the focus on mobile clients it becomes important to expose these services as REST APIs to support new consumers at the same time ensuring that existing customers (SOAP clients) are not impacted.
As a service producer you want to ensure that your existing service can be consumed by new consumers without making any changes to the business backend service.

Solution
Oracle Service Bus addresses these challenges with minimum effort. To show this let's take a simple example. In this example we use a Credit Card validation service as the business back end service which is virtualized using Oracle Service Bus.
Clients do not call the service directly but via proxy services defined within OSB which routes the request to backend service via business service. Since we are using Oracle Service Bus we can simply add a new REST based proxy service to support our use case. Let's see how.
This diagram below shows the OSB configuration project inside oracle jdeveloper 12c.
There are 3 parts
1) ValidatePS - Proxy Service - Interface which the service consumer/client calls.
2) ValidatePP - Pipleline/Splitjoin - does message processing between proxy and business service.
3) validateBS - Business Service - calls the actual backend service.
There are 3 parts
1) ValidatePS - Proxy Service - Interface which the service consumer/client calls.
2) ValidatePP - Pipleline/Splitjoin - does message processing between proxy and business service.
3) validateBS - Business Service - calls the actual backend service.
To expose your back-end service as REST serve all you need to do is right click on OSB pipeline and select "Expose as REST" option.
This should open a dialog box where you can specify REST binding properties like name, arguments, HTTP method type etc.
This should generate the corresponding proxy service for REST
Now as you can see the Oracle service bus exposed 2 proxy services to which service consumers can connect to, one REST proxy and other the existing SOAP proxy service.
You can test your REST proxy by doing a right click and select run.
This should open up a Proxy service test page where you can provide the values which are expected by Business backend service e.g Credit card number, expiry, amount etc.