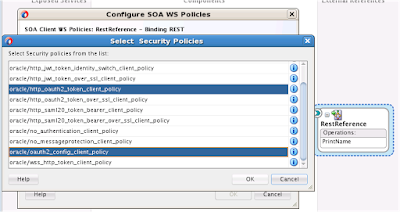
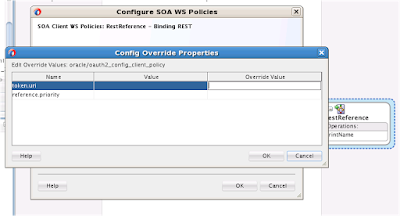
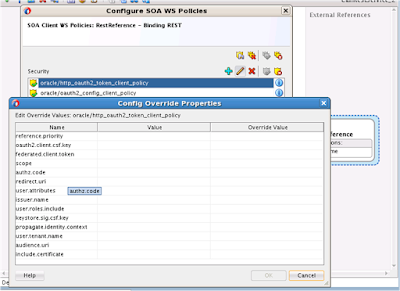
In my blog about Identity and Access Management i explained about what is IDM at a high level. There are several vendors which provides products for IDM implementation. The latest
on-premise offering (as of today) is 11.1.2.3.0 which is 3rd patchset release of Oracle Identity and access Management. Before using this let's go through the high level steps to install and configure it.
Prerequisite: Ensure that you have an Oracle Database installed on your system before installing Oracle Identity and Access Management. The database must be up and running to install the relevant Oracle Identity and Access Management components.
Also please go through the Read Me info for Oracle Identity and Access Management 11g Release 2 before proceeding with installation
Here are the high level steps -
1) Run Repository Creation Utility (RCU) to create and load the appropriate schemas
2) Install Weblogic server and create Middleware Home
3) Install Oracle Identity and Access Management from IDM shiphome suite
4) Confiure IDM Suite and create domain
5) Configure Security Store
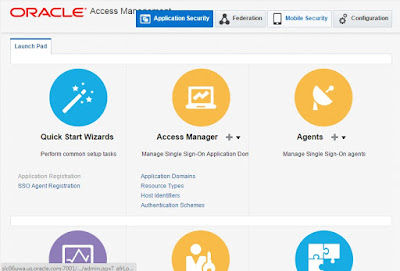
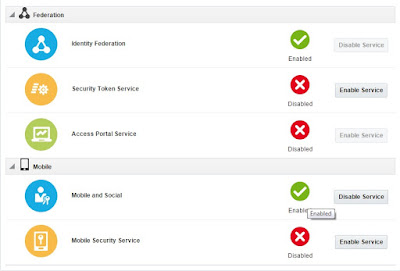
6) Start servers and Verify product consoles (WLS/EM/OAM) are reachable
In this blog i have downloaded the required installation files from -
http://www.oracle.com/technetwork/middleware/id-mgmt/downloads/oid-11gr2-2104316.html
on my Linux x86_64 machine
Let's deal with them in detail -
# unzip rcuHome.zip -d /scratch/gaurasha/rcuHome
b) Run the rcu utility
# cd /scratch/gaurasha/rcuHome/bin
# ./rcu
c) Select Create

Provide your database details -

Create a new prefix e.g DEV and select the required component you wish to install e.g
Oracle Acccess Manager. Dependencies will be automatically selected.

Click Next

choose a password

Click Next. This should create and load the required schemas for Oracle IDM products into your database.
a. Execute the WLS installation (install the appropriate version for your platform)


# cd /scratch/gaurasha/middleware/oracle_common/common/bin
Execute following command
# sh wlst.sh /scratch/gaurasha/middleware/Oracle_IDM1/common/tools/configureSecurityStore.py -d /scratch/gaurasha/middleware/user_projects/domains/idm_domain -c IAM -m create -p welcome1
on-premise offering (as of today) is 11.1.2.3.0 which is 3rd patchset release of Oracle Identity and access Management. Before using this let's go through the high level steps to install and configure it.
Prerequisite: Ensure that you have an Oracle Database installed on your system before installing Oracle Identity and Access Management. The database must be up and running to install the relevant Oracle Identity and Access Management components.
Also please go through the Read Me info for Oracle Identity and Access Management 11g Release 2 before proceeding with installation
Here are the high level steps -
1) Run Repository Creation Utility (RCU) to create and load the appropriate schemas
2) Install Weblogic server and create Middleware Home
3) Install Oracle Identity and Access Management from IDM shiphome suite
4) Confiure IDM Suite and create domain
5) Configure Security Store
6) Start servers and Verify product consoles (WLS/EM/OAM) are reachable
In this blog i have downloaded the required installation files from -
http://www.oracle.com/technetwork/middleware/id-mgmt/downloads/oid-11gr2-2104316.html
on my Linux x86_64 machine
| rcu | /scratch/gaurasha/idmr2ps3-artifacts/rcuHome.zip |
| Weblogic Installation | /scratch/gaurasha/idmr2ps3-artifacts/wls1036_linux32.bin |
| IDM suite |
/scratch/gaurasha/idmr2ps3-artifacts/iamsuite1.zip
/scratch/gaurasha/idmr2ps3-artifacts/iamsuite2.zip
/scratch/gaurasha/idmr2ps3-artifacts/iamsuite3.zip
|
Let's deal with them in detail -
1) Run Repository Creation Utility (RCU) to create and load the appropriate schemas
a) Copy the appropriate rcuHome.zip to <dir> with plenty of space.# unzip rcuHome.zip -d /scratch/gaurasha/rcuHome
b) Run the rcu utility
# cd /scratch/gaurasha/rcuHome/bin
# ./rcu
c) Select Create

Provide your database details -

Create a new prefix e.g DEV and select the required component you wish to install e.g
Oracle Acccess Manager. Dependencies will be automatically selected.

Click Next

choose a password

Click Next. This should create and load the required schemas for Oracle IDM products into your database.
2) Install Weblogic server and create Middleware Home
# cd /scratch/gaurasha/idmr2ps3-artifacts/
# ./wls1036_linux32.bin
b. Choose a new Oracle Middleware home

c. Click Next -> choose Typical installation
This should install WLS server along with jdk in the selected middleware location.
3) Install Oracle Identity and Access Management from IDM shiphome suite
a. Unzip IDM Suite zip files to a location with plenty of space
# mkdir /scratch/idm
# cd /ade_autofs/gd17_fmw/IDM_11.1.2.2.0_GENERIC.rdd/140103.0922/idm/shiphome/
# unzip iamsuite1.zip -d /scratch/idm
# unzip iamsuite2.zip -d /scratch/idm
# unzip iamsuite3.zip -d /scratch/idm
# cd /scratch/idm/iamsuite/Disk1
b. Run the IDM Installation prog (make sure you specify the correct path for Java JDK)./runInstaller -jreLoc /scratch/gaurasha/middleware/jdk160_29
c. For first time installations you may need to specify inventory directory location
You can choose to skip software updates.
Click Next
Provide location of Middleware home and click Next
Click Install to complete Installation
# unzip iamsuite1.zip -d /scratch/idm
# unzip iamsuite2.zip -d /scratch/idm
# unzip iamsuite3.zip -d /scratch/idm
# cd /scratch/idm/iamsuite/Disk1
b. Run the IDM Installation prog (make sure you specify the correct path for Java JDK)./runInstaller -jreLoc /scratch/gaurasha/middleware/jdk160_29
c. For first time installations you may need to specify inventory directory location
4) Configure IDM and create domain
b. Create a new Weblogic domain
Select -> Oracle Access Management and Mobile security Suite and click Next
Provide domain name
Provide password for OAM admin console e.g welcome1
Test JDBC component schema and click Next
Domain creation should succeed.
Click Next
Configure JDBC Component Schema: Password: welcome1

5) Configure Security Stores
Prior to starting the admin server, make sure to execute the following command (default OPSS_SCHEMA_PASSWORD is welcome1)# cd /scratch/gaurasha/middleware/oracle_common/common/bin
Execute following command
# sh wlst.sh /scratch/gaurasha/middleware/Oracle_IDM1/common/tools/configureSecurityStore.py -d /scratch/gaurasha/middleware/user_projects/domains/idm_domain -c IAM -m create -p welcome1
Here
/scratch/gaurasha/middleware/user_projects/domains/idm_domain is domain path
created in step 4
created in step 4
6) Start servers and verify Installation
# cd /scratch/gaurasha/middleware/user_projects/domains/base_domain/bin
# sh startWeblogic.sh
# sh startManagedWebLogic.sh oam_server1 http://localhost:7001
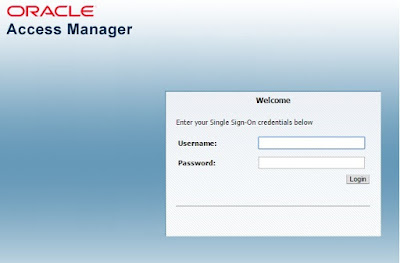
Go to following URLs to verify the product consoles are reachable:
# sh startManagedWebLogic.sh oam_server1 http://localhost:7001
Go to following URLs to verify the product consoles are reachable:
Weblogic Admin console - http://host:7001/console